Incident reporting
Our customers are the first line of defense against cybersecurity threats, and detecting threats and incidents quickly reduces the possibility of any negative consequences. Towards that end, the information below explains how to detect security threats and report them to the DocuSign information security team for investigation.
Dedicated threat reporting channels
To make it easier to report suspicious activities, DocuSign has dedicated reporting channels based on the type of threat:
- DocuSign-themed fraudulent emails and websites: if you think that you’ve received a fraudulent email purporting to come from DocuSign, forward the entire email as an attachment to spam@docusign.com and delete it immediately.
- DocuSign account misuse and/or abuse: if you suspect that a DocuSign account has been misused, please send the details of this threat and/or incident to securityaccountabuse@docusign.com. Examples of activities to report include illegal activity, impersonation of another person or business as a sender or signer, and improper solicitation of financial or personal information. You’ll need to include the following information, as relevant, when reporting:
- Your full name and contact information
- Envelope ID, attachments, screenshots, and forms
- Customer/sender name (business/individual) and email address
- Any known customer/sender identifiers not included in the envelope email (e.g. physical address, phone number, etc.)
- Any other information you deem pertinent
Please note: we don’t access envelope contents in the DocuSign system, even if authorized by the complainant.
- Other security incidents and DocuSign-themed threats for investigation: new cybersecurity threats occur all the time. To support DocuSign information security and threat intelligence, please report security incidents and DocuSign platform threats to security@docusign.com for investigation.
Threat-detection guidelines for fraudulent emails and websites
First and foremost, if you don’t recognize the sender of a DocuSign envelope and you’re uncertain of the email’s authenticity, look for the unique security code included in all DocuSign envelopes at the bottom of the notification email. If you don’t see this code, don’t click on any links or open any attachments within the email. For more information, please review our Combating Phishing white paper.
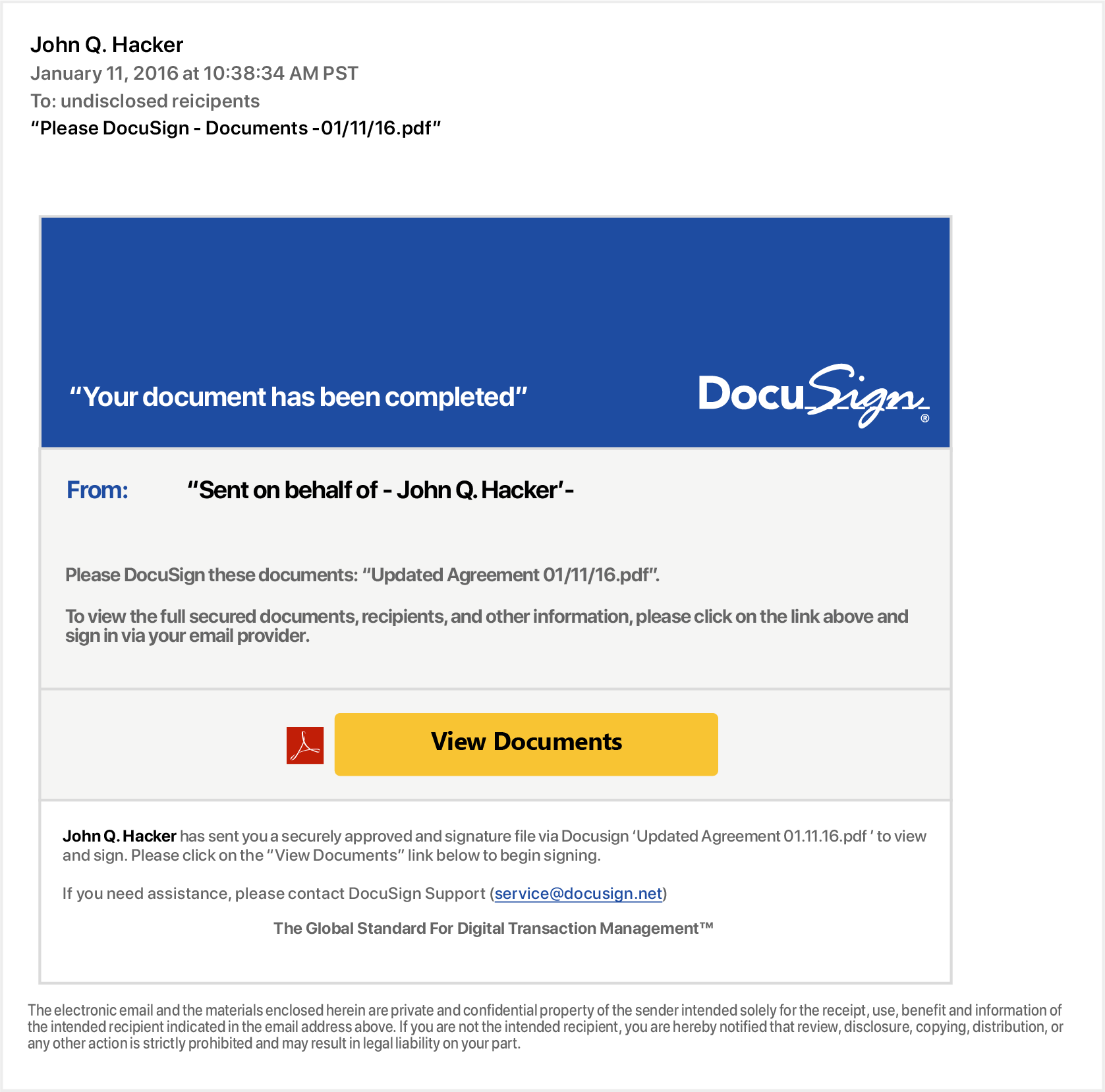
Signs of fraudulent emails and websites
- Fake links
Avoid fake links by accessing your documents directly from https://www.docusign.com using the unique security code found at the bottom of the DocuSign notification email.
Always check where a link goes before you click on it by hovering your mouse over the link to look at the URL in your browser or email status bar (they should be hosted on docusign.com or docusign.net). A fraudulent link is dangerous and can:
- Direct you to a fake website that tries to collect your personal data
- Install spyware on your system (spyware is an application that can enable a hacker to monitor your actions and steal any login IDs, passwords, or credit card numbers you type)
- Cause you to download a virus that could disable your computer
- Fake sender email address
Fake emails may include a forged email address in the "From" field, which is easily altered. If you don’t recognize the sender of a DocuSign envelope, contact the sender to verify the authenticity of the email.
- Attachments
DocuSign emails that request you to sign a document never contain attachments of any kind. Don’t open or click on attachments within an email requesting your signature. DocuSign emails only contain PDF attachments of completed documents after all parties have signed the document. Even then, pay close attention to the attachment to ensure it’s a valid PDF file. DocuSign never attaches zip files or executables.
- Generic greetings
Many fake emails begin with a generic greeting like “Dear DocuSign Customer.” If you don’t see your name in the salutation, be suspicious and don’t click on any links or attachments.
- False sense of urgency
Many fake emails try to deceive you with the threat that your account is in jeopardy if you don’t provide immediate updates. They may also state that unauthorized transactions have occurred on your account or that DocuSign needs to update your account information immediately.
- Emails that appear to be websites
Some fake emails are made to look like a website to get you to enter personal information. DocuSign never asks you for personal information, including login, ID, or password, via an email.
- Deceptive URLs
Check the Web address. Just because the address looks OK, don't assume you're on a legitimate site. Look in your browser's URL bar for signs that you may be on a phishing site:
- Often the Web address of a phishing site looks correct but actually contains a common misspelling of the company name or a character or symbol before or after the company name, such as docusing.com instead of docusign.com
- Look for tricks like substituting the number "1" for the letter "l" in a Web address or transposing consecutive letters of the brand, such as rea1estate.docusign.com instead of realestate.docusign.com
- Your browser has ways of detecting certain types of malicious sites—always heed these browser warnings, especially when they notify you that the site or certificate can’t be trusted
- Misspellings and bad grammar
While no one is perfect, fake emails often contain misspellings, incorrect grammar, missing words, and gaps in logic. Mistakes like this help fraudsters avoid spam filters.
- Unsafe sites
The term "https" should always precede any website address where you enter personal information. The "s" stands for secure. If you don't see "https," you're not in a secure Web session, and you shouldn’t enter any personal data. A legitimate DocuSign sign-in page address always starts with “https://” not “http://.”
- Pop-up boxes
DocuSign never uses a pop-up box in an email, because pop-ups aren’t secure.
Threat-detection guidelines for account abuse
The following are guidelines for detecting account abuse threats:
- Is the sender a DocuSign customer (did the message come from docusign.net or docusign.com)?
- Did the sender use their account to engage in illegal activity or commit fraud?
- Did the sender improperly solicit personal or sensitive information?
- Did the sender impersonate a DocuSign customer or was a signer impersonated?
- Is the sender in violation of any other DocuSign terms of conditions outlined under Section 5: Restrictions on Use of the site (5.1)?
If the answer is yes to any of these questions, send details to securityaccountabuse@docusign.com.